About FLAME
FLAME is a handy tool for evaluating anomaly detection systems operating at the flow level. FLAME takes a serial stream of flows in Netflow v5, Netflow v9 or IPFIX format as input, injects anomalies according to a given injection schedule, and outputs the modified trace in the input format. The modified traces can then be fed to an anomaly detection system to test whether it succeeds or fails to detect the injected anomalies. The usage of FLAME for detector evaluation is illustrated in the figure below.
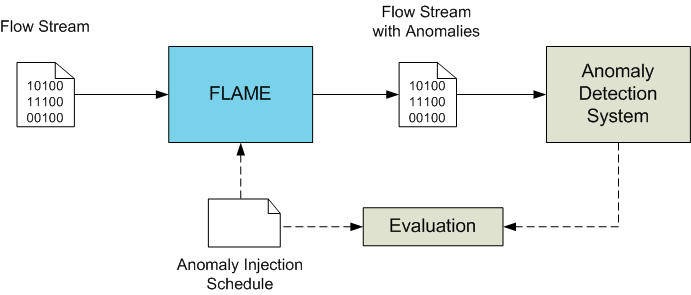
The core framework including flow input, output and internal flow handling is written in C++ for performance reasons. FLAME comes with a standard library of several anomaly models for scans, denial of service attacks, and spam. Anomaly models are written in Python to give flexibility to the user. The core framework consists of several modules communicating via named pipes.
Anomaly Models
To keep the involved complexity at a manageable level, we decided to include three groups of flow attributes in our models: i) IP address and port number sequences per flow, ii) flow size (in bytes and packets) and flow duration (in milliseconds), and iii) flow inter-arrival times. We consciously disregard other flow attributes such as the IP type of service (TOS) or SNMP input/output interfaces as they are not as important for anomaly detection purposes. For TCP anomalies we additionally include the TCP flags.
Each flow attribute is represented by a stochastic model that is called a generation function in our terminology. Dependencies or correlation between different flow attributes can be captured in the model by using if then clauses in the Python code. FLAME currently supports three different generation functions: constant, random and periodical. These generation functions are implemented in C++ and can be called from the Python code via embedded scripting. The models included in the standard library have been extracted manually from two weeks of unsampled flow traces that were captured in the SWITCH backbone network.
